Have a question about how the new message protection capabilities work? Check for an answer here. Also, take a look at Frequently asked questions about data protection in Azure Information Protection for answers to questions about the data protection service, Azure Rights Management, in Azure Information Protection.
What is Office 365 Message Encryption (OME)?
There’s no one-size-fits-all solution. One thing is for sure: you will set yourself up for success by only using business communication methods you need and will actually use. For example: You want a forum board, so you and your staff spend weeks finding the best solution and setting it up. One size of continuous improvement doesn't fit all parts of the organization. The kind of rigor required in a manufacturing environment may be unnecessary, or even destructive, in a research. The 'brilliant' marketing messages came from my own imagination and were influenced by this great list of legendary tag-lines. Helps entrepreneurs change the world. Get the advice you need to. You may already have some basic templates to work from. If not, find a template online or just start from scratch. You need to write the plan to fit your corporate culture or a tone your organization is accustomed to, from a very formal format to a more casual, upbeat tone.
OME combines email encryption and rights management capabilities. Rights management capabilities are powered by Azure Information Protection.
Who can use OME?
You can use the new capabilities for OME under the following conditions:
If you have never set up OME or IRM for Exchange Online in Office 365.
If you have set up OME and IRM, you can use these steps if you are using the Azure Rights Management service from Azure Information Protection.
If you are using Exchange Online with Active Directory Rights Management service (AD RMS), you can't enable these new capabilities right away. Instead, you need to migrate AD RMS to Azure Information Protection first. When you've finished the migration, you can successfully set up OME.
If you choose to continue to use on-premises AD RMS with Exchange Online instead of migrating to Azure Information Protection, you will not be able to use these new capabilities.
What subscriptions do I need to use the new OME capabilities?
To use the new OME capabilities, you need one of the following plans:
Office 365 Message Encryption is offered as part of Office 365 Enterprise E3 and E5, Microsoft Enterprise E3 and E5, Microsoft 365 Business Premium, Office 365 A1, A3, and A5, and Office 365 Government G3 and G5. Customers do not need additional licenses to receive the new protection capabilities powered by Azure Information Protection.
You can also add Azure Information Protection Plan 1 to the following plans to receive the new Office 365 Message Encryption capabilities: Exchange Online Plan 1, Exchange Online Plan 2, Office 365 F1, Microsoft 365 Business Basic, Microsoft 365 Business Standard, or Office 365 Enterprise E1.
Each user benefiting from Office 365 Message Encryption needs to be licensed to be covered by the feature.
For the full list see the Exchange Online service descriptions for Office 365 Message Encryption.
Can I use Exchange Online with bring your own key (BYOK) in Azure Information Protection?
Yes! Microsoft recommends that you complete the steps to set up BYOK before you set up OME.
For more information about BYOK, see Planning and implementing your Azure Information Protection tenant key.
Do OME and BYOK with Azure Information Protection change Microsoft's approach to third-party data requests such as subpoenas?
No. OME and the option to provide and control your own encryption keys, called BYOK, from Azure Information Protection were not designed to respond to law enforcement subpoenas. OME, with BYOK for Azure Information Protection, was designed for compliance-focused customers. Microsoft takes third-party requests for customer data very seriously. As a cloud service provider, we always advocate for the privacy of customer data. In the event we get a subpoena, we always attempt to redirect the third party to the customer to obtain the information. (Please read Brad Smith's blog: Protecting customer data from government snooping). We periodically publish detailed information of the request we receive. For more information regarding third-party data requests, see Responding to government and law enforcement requests to access customer data on the Microsoft Trust Center. Also, see 'Disclosure of Customer Data' in the Online Services Terms (OST).
How is this feature related to legacy Office 365 Message Encryption (OME) and Information Rights Management (IRM) features?
The new capabilities for Office 365 Message Encryption are an evolution of the existing IRM and legacy OME solutions. The following table provides more details.
Comparison of legacy OME, IRM, and new OME capabilities
| Capability | Previous versions of OME | IRM | New OME capabilities |
|---|---|---|---|
| Sending an encrypted email | Only through Exchange mail flow rules | End-user initiated from Outlook for Windows, Outlook for Mac, or Outlook on the web; or through Exchange mail flow rules | End-user initiated from Outlook for Windows, Outlook for Mac, or Outlook on the web; or through mail flow rules |
| Rights management | - | Do Not Forward option and custom templates | Do Not Forward option, encrypt-only option, default and custom templates |
| Supported recipient type | External recipients only | Internal recipients only | Internal and external recipients |
| Experience for recipient | External recipients received an HTML message that they downloaded and opened in a browser or downloaded mobile app. | Internal recipients only received encrypted email in Outlook for Windows, Outlook for Mac, and Outlook on the web. | Internal and external recipients receive email in Outlook for Windows, Outlook for Mac, Outlook on the web, Outlook for Android, and Outlook for iOS, or through a web portal, regardless of whether or not they are in the same organization or in any organization. The OME portal requires no separate download. |
| Bring Your Own Key support | Not available | Not available | BYOK supported |
How do I enable the new OME capabilities for my organization?
See Set up new Office 365 Message Encryption capabilities.
Will the previous version of OME be deprecated?
You can still use the previous version of OME, it will not be deprecated at this time. However, we highly encourage organizations to use the new and improved OME solution. Customers that have not already deployed OME cannot set up a new deployment of the previous version of OME.
My organization uses Active Directory Rights Management, can I use this functionality?
No. If you are using Exchange Online with Active Directory Rights Management service (AD RMS), you can't enable these new capabilities right away. Instead, you need to migrate AD RMS to Azure Information Protection first.
My organization has an Exchange Hybrid deployment. Can I use this feature?
On-premises users can send encrypted mail using Exchange Online mail flow rules. In order to do this, you need to route email through Exchange Online. For more information, see Part 2: Configure mail to flow from your email server to Microsoft 365.
What email client do I need to use in order to create an OME encrypted message? What applications are supported for sending protected messages?
You can create protected messages from Outlook 2016, Outlook 2013 for Windows and Mac, and from Outlook on the web. For more information on sending encrypted messages, see Send, view, and reply to encrypted messages in Outlook for PC.
What email clients are supported to read and reply to protected emails?
One Message Does Not Fit All: Why You Need An Email Plans
Microsoft 365 users can read and respond from Outlook for Windows and Mac (2013 and 2016), Outlook on the web, and Outlook mobile (Android and iOS). You can also use the iOS native mail client if your organization allows it. If you are not a Microsoft 365 user, you can read and reply to encrypted messages on the web through your web browser.
What email clients support the encrypt-only protected emails?
Microsoft 365 users can use Outlook for PC versions 2019 and Microsoft 365 to create mail protected with the encrypt-only policy. That means messages that have the new encrypt-only policy applied can be read directly in Outlook on the web, in Outlook for iOS and Android, and now Outlook for PC versions 2019 and Microsoft 365.
Is there a size limit for messages you can send with OME?
Yes. The maximum message size you can send with OME, including attachments, is 25 MB. For more information, see Message limits.
What file types are supported as attachments in protected emails? Do attachments inherit the protection policies associated with protected emails?
You can attach any file type to a protected mail. With one exception, protection policies are applied only on the file formats mentioned in File types supported by the Azure Information Protection client. OME does not support the 97-2003 versions of the following Office programs: Word (.doc), Excel (.xls), and PowerPoint (.ppt).
If a file format is supported, such as a Word, Excel, or PowerPoint file, the file is always protected, even after the attachment has been downloaded by the recipient. For example, say an attachment is protected by Do Not Forward. The original recipient downloads the file, creates a message to a new recipient and attaches the file. When the new recipient receives the file, the recipient will not be able to open the protected file.
Are PDF file attachments supported?
The short answer is yes! PDF encryption allows you to protect sensitive PDF documents through secure communication or secure collaboration. When you send email, the Office 365 service encrypts PDF file attachments not the Outlook client.
For Outlook on the web, Outlook for iOS, and Outlook for Android, you can encrypt PDFs you send without any additional steps. These clients natively support PDF encryption.
Outlook desktop does not natively support encryption of PDF file attachments. Instead, you'll need to set up Exchange mail flow rules or DLP to apply encryption to PDF attachments first. When you send mail from Outlook Desktop with a PDF attachment, the client sends the message with the attachment to the service first. When the service receives the file, the service applies the OME protection of the data loss prevention (DLP) policy or mail flow rule in Exchange Online. Next, Exchange Online sends the message with the protected PDF file attachment.
To enable encryption for PDF attachments, run the following command in Exchange Online PowerShell:
PDF encryption allows you to protect sensitive PDF documents through secure communication or secure collaboration. For all Outlook clients, messages and unprotected PDF attachments inherit the OME protection of the data loss prevention (DLP) policy or mail flow rule in Exchange Online. Also, if an Outlook on the web user attaches an unprotected PDF document and applies protection to message, the message inherits the protection of the message. Users can only open the encrypted attachments in applications that support protected PDFs (for example, the OME Portal and the Azure Information Protection Viewer).
Important
Outlook desktop client does not support PDF encryption.
Are OneDrive for Business attachments supported?
Not yet. OneDrive for Business attachments are not supported and end-users can't encrypt a mail that contains a cloud OneDrive for Business attachment.
What email clients support preview of encrypted attachments in protected emails?
When attachments are protected with a protected mail, Outlook clients provide tha ability to preview the document directly. Outlook supports preview of Office documents (docx, xlsx, pptx, doc, xls, ppt). Outlook on the web supports preview of Office documents (docx, xlsx, pptx) and PDF.
What email clients support revocation of protected emails?
Outlook on the web supports revocation of protected mail. See How to revoke an encrypted message that you sent for details.
Can I automatically encrypt messages by setting up policies?
Yes. Use mail flow rules in Exchange Online to automatically encrypt a message based on certain conditions. For example, you can create policies that are based on recipient ID, recipient domain, or on the content in the body or subject of the message. See Define mail flow rules to encrypt email messages in Office 365.
Can I automatically remove encryption on incoming and outgoing mail?
Admins can set up a mail flow rule to remove encryption for outgoing mail. You can't set up a rule to remove encryption for incoming mail.
Can I automatically encrypt messages by setting up policies in Data Loss Prevention (DLP) through the Security & Compliance Center?
Yes! You can set up mail flow rules in Exchange Online or by using DLP in the Security & Compliance Center.
Can I customize encrypted messages with my company branding?
Yes! For information on customizing email messages and the OME portal, see Add your organization's brand to your encrypted messages. See Add your organization's brand to your encrypted messages.
Are there any reporting capabilities or insights for encrypted emails?
There is an Encryption report in the Security and Compliance Center. See View email security reports in the Security & Compliance Center.
Can I use message encryption with compliance features such as eDiscovery?
Yes. All encrypted email messages are discoverable by Microsoft 365 compliance features.
Can I remove encryption from email?
Admins can set up a mail flow rule to remove encryption from outgoing mail. You can't remove encryption using a mail flow rule from incoming messages.
Is delegated access supported?
Not at this time.
Can I open encrypted messages sent to a shared mailbox?
Yes! Encrypted messages are supported for a shared mailbox.
Users can open protected mails in a shared mailbox where the shared mailbox received a protected mail as part of a distribution group.
Users can view attachments that inherit protection from email when they use Outlook for Windows, Outlook for Mac, and Outlook on the web.
The following table lists the supported clients for shared mailboxes.
| Platform | Read mail | View email attachments |
|---|---|---|
| Outlook on the web | Yes | Yes |
| Outlook for Windows | Yes | Yes |
| Outlook for Mac | Yes | Yes |
| Outlook for Android | Yes | No |
| Outlook for iOS | Yes | No |
There are currently two known limitations:
You can't open attachments to emails that you receive on mobile devices by using Outlook mobile.
We don't support assignment through an email enabled security group. We only support access provided by direct user assignment to the shared mailbox and that automapping is enabled for Exchange Online. Automapping is enabled by default for Exchange Online.
To assign a user to the shared mailbox
Connect to Exchange Online Using Remote PowerShell.
Run the Add-MailboxPermission cmdlet with the Automapping parameter. This example gives Ayla full access permissions to a support mailbox.
What do I do if I don’t receive the one-time pass code after I requested it?
First, check the junk or spam folder in your email client. DKIM and DMARC settings for your organization may cause these emails to end up filtered as spam.

Next, check quarantine in the Security & Compliance Center. Often, messages containing a one-time pass code, especially the first ones your organization receives, end up in quarantine.
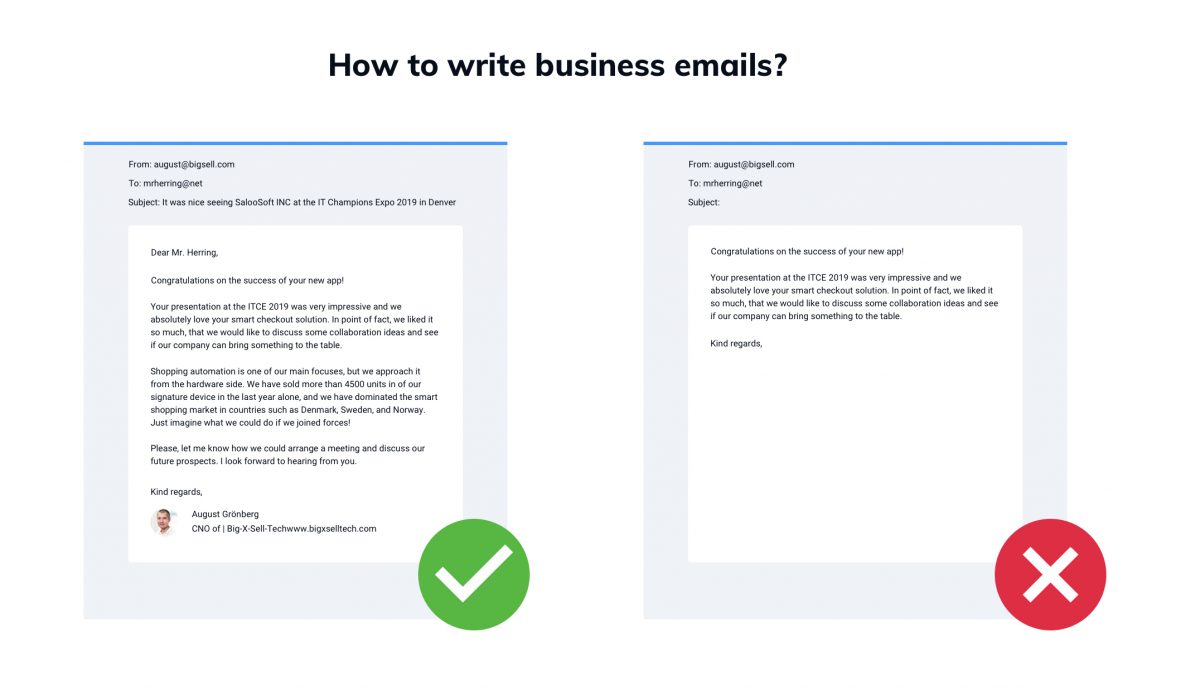
Starting out an email with the right greeting is crucial. It gives recipients their first impression of you, and it sets the tone for the rest of the message. It can mean the difference between your recipient closing the email right away (and condemning it to the trash folder), or reading on.
In short, you need that first impression to be a positive one.
But that’s not to say that the same greeting works in all circumstances. You need to tailor your greeting to suit the type of email you’re sending and the recipient(s) you’re sending it to. And while that might feel like an impossible task with all of the different possibilities out there, it’s not as hard as it might seem. Here’s how to start an email, plus 50 key greetings you can try for various situations.
Starting an email
There are no hard-and-fast rules about how to start an email. In the past, there were strict rules about using “Dear” followed by a surname in any formal letter or email. Under no circumstances would you reach out to a perfect stranger and say “Hey!”
Nowadays, the lines are more blurred. It all boils down to how well you know the recipient, the context of the message, and what you’re expecting to achieve as a result of your email.
From a punctuation point of view, there are still some rules that are worth following. Start by putting a comma after the email greeting, and then capitalize the first letter of the opening sentence. For example:
“Dear Mrs. Smith,
I’m writing to you in response to …”
ADD_THIS_TEXT
5 Best Practices on How to Start an Email
1. Find the Right Contact

When sending a cold email, it’s important to make an effort to personalize your message – it’s no secret that a personalized email is more likely to be opened, read, and acted upon than a generic mailshot.
Whenever possible, do your research and find out exactly who you need to be sending your email to. For starters, try to find a direct email address rather than a generic help desk email. Then, do your best to find the most relevant person to reach out to. If you’re hoping to promote email marketing software but reach out to the head of public relations, you’re reducing your chances of success.
2. Determine the Goal/Purpose of Your Email
Whether you’re carrying out a mass email marketing campaign or writing a bespoke email to a known recipient, it’s always useful to keep the purpose of your email in mind.
Your goal might be to introduce yourself or your business for the first time (cold outreach); recover a lost lead or dormant customer; or simply to send out your monthly newsletter. Whatever it is, knowing the purpose of your email and its context will help you to start it in the most appropriate way.
3. If in Doubt, Err Towards Being More Formal
A personalized email is generally more engaging than a formal one, but sometimes being too relaxed can rub people up the wrong way. If you’re not sure what tone to take, your safest bet is to be a bit more formal rather than overly friendly. Then, you can adjust your tone based on the response you receive, if necessary.
4. Watch Your Grammar
A surefire way of giving your recipient a bad first impression is to mess up on your grammar. When it comes to starting your email, the main punctuation you need to worry about is the comma after the recipient’s name.
Whether or not you choose to include a comma is not important. Consistency is. As a rule of thumb, if you use a comma after the salutation, then use one at the end of your letter when you sign off.
5. Consider the Context of the Message
Lastly, for your email to make sense (and therefore make an impact), the greeting should be in keeping with the rest of your message. The tone, purpose, and style of your email must be reflected in the way you address the recipient. If there’s a mismatch, then you risk causing confusion.
Say you’re sending a message to a loyal customer to announce they’ve been carefully selected to benefit from an exciting new promotion. The context of the message would suggest you’d address the email in a personalized and friendly manner, such as “Hey [first name]!” To start it with “Dear sir/madam” would be incongruous and confusing.
Additional Reading:5 Introduction Email Templates That Work in 2020
Cold Email Greetings
When you’re reaching out to a contact with whom you have no prior connection, it’s important to get the tone right. If you’re overly familiar, you’ll turn them off right away and probably end up in the junk folder. So, in those cases, whether or not you know their name, it’s always best to stay formal.
If you don’t know their name:
It’s tricky if you’re reaching out over email but don’t have a specific name. Do your best to find a contact name, even if it’s not the exact person you’re trying to get ahold of. However, if you really can’t find it, then the following are still broadly acceptable greetings:
1. “Dear sir/madam”
2. “To whom it may concern”
3. “To…” e.g. “To the Financial Director”
If you do know their name:
4. “Dear Mr./Mrs./Ms. [surname]”
5. Dear [first name]
Cold emails are always best if you’ve done some research beforehand. That way, you can add some personalized context immediately after your greeting. For example:
“Dear Mr. Smith,
I really enjoyed your last article about …”
Any form of personalization softens your cold email greeting, and makes it much more likely that the recipient will read on.
Informal Greetings
Informal email greetings are those we use every day: with our bosses, our families, and our friends and acquaintances. That said, relaxed email greetings are increasingly being used in traditionally formal contexts like the cold outreach emails we’ve just discussed. How and when you use them entirely depends on your brand style and voice:
6. “Dear [first name]”
7. “Hello”
8. “Hi”
9. “Hey”
10. “I hope this email finds you well”
11. “I hope you enjoyed your weekend”
12. “I hope you’re doing well”
13. “Hope you’re having a great week”
14. “How are you doing?”
15. “How’s it going?”
16. “I’d love to get your advice on …”
17. “Long time no see”
18. “It’s been a while”
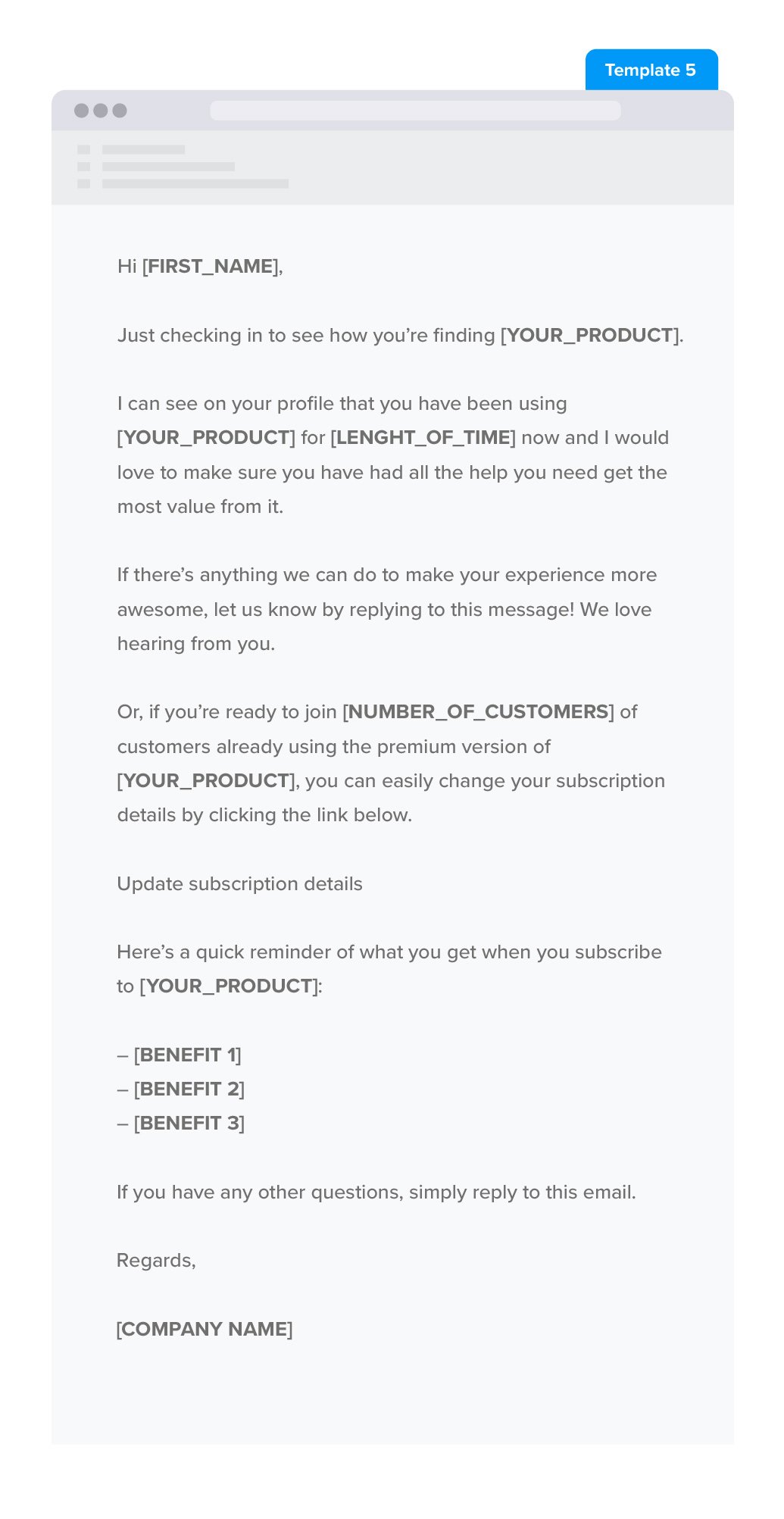
Follow-up Greetings
Follow-up emails are easy to start, because you’ve got the perfect prompt to kick you off. They also allow you to get to the point quickly:
19. “As we discussed on our phone call …”
20. “As promised, here’s …”
21.“I’m checking in on …”
22. “Following up on our meeting …”
23. “Can you please provide me an update on …”
24. “Here’s more information on …”
25. “It was great to meet you at [event]”
Reply Emails
Replying to an email is similar to writing a follow-up email. It allows you to ping back a response with a straightforward greeting:
26. “Thanks for the quick response”
27. “Thanks for getting back to me”
28. “Thanks for the update”
29. “Great to hear from you”
Time of Day
Using the time of day as a message opener is always a winner – it’s friendly, yet relatively formal:
30. “Good morning” (Before midday)
31. “Good afternoon” (Midday until 6 p.m.)
32. “Good evening” (6 p.m. onwards)
33. “G’day” (used in Australia)
A Response to a Trigger
When something has triggered you to write an email, you can often get away with not using a salutation like “Dear” or even “Hi.” It’s perfectly acceptable to make the thing you’re writing about form the greeting itself. For example, if your contact has just won a prize, it would be odd to write:
“Dear Sarah,
Congratulations on winning the top prize at …”
Instead, this would seem more natural:
“Congratulations on winning the top prize, Sarah! I knew you could do it!”
So, if you’re about to start about an email, think about the context in which you’re writing it, and consider using that contextual trigger as your opener:
34. “Congratulations on …”
One Message Does Not Fit All: Why You Need An Email Planner
35. “I hope you enjoyed your [vacation/event]”
36. “I love your recent [article/social post/photo/video]”
37. “I was just thinking about you”
38. “This reminded me of you”
39. “[Mutual friend/contact] reminded me to get in touch with you”
Writing to Several People
You have a few choices when writing to more than one recipient at a time. Try starting your message with “Hi everyone,” or:
40. “Hi [first name 1], [first name 2], and [first name 3],”
When someone sees their name in a list, they’re more likely to open the email and read it.
Slang Greetings
One Message Does Not Fit All: Why You Need An Email Planning
These greetings should be reserved for people you know well and with whom you share a more colloquial lingo. Often these greetings are the domain of younger generations, but not necessarily:
41. “Yo”
42. “Alright”
43. “Howdy”
44. “ ‘Sup ”
Humorous Greetings
Reaching out with humor can be a useful way of breaking the ice. This style is often used in promotional sales emails to increase open and read rates.
But you should be sure of your audience, or it could make things awkward. Best to use a lightness of tone, rather than a full-blown joke:
45. “Happy Hump Day”
46. “Only x days til Friday”
47. “Happy Fri-YAY!”
One Message Does Not Fit All: Why You Need An Email Plan Template
48. “Hope you’re surviving”
49. “Had your coffee?”
50. “Me again …”
It might also be worth getting creative with your greetings, using emojis ✋ or gifs to add something extra.
Upgrade Your Email Account with Right Inbox
With so much of our communications taking place over email, it can be challenging to keep our inboxes under control. That’s why we created Right Inbox – a simple plugin that can help you spend less time in your inbox and more time being productive.
For example, with our email reminders feature, you can snooze emails and ensure they’ll pop back up to the top of your inbox when you’re ready to reply, forever removing the risk of forgetting to follow up. In addition, our email tracking feature allows you to view exactly how many times your email has been viewed and by whom, so you can plan your follow-ups accordingly.
ADD_THIS_TEXT
In summary
When you’re kicking off an email, you need to be conscious of who you’re writing to and the context of the message. Both will determine how you craft those all-important opening words.
A well-written salutation will determine how well the rest of your message will be received, regardless of whether you’re contacting a potential client or your best friend. Hopefully this list will help you pick the right words to fit the right circumstances, so feel free to use these ideas in your day-to-day correspondence.
